Implementing Zero Trust Architecture: A Practical Guide
Security for a Borderless World
Over the past decade, the way companies operate has changed dramatically. Remote work, cloud computing, mobile access, and a growing web of third-party services have all blurred the once-clear lines of the corporate network. In this new IT environment, traditional security models, which were built around the idea that everything inside the network perimeter can be trusted, are no longer enough.
Zero Trust Architecture (ZTA) is a security concept that addresses this reality. Based on the principle of “never trust, always verify,” Zero Trust assumes that threats can come from anywhere, inside or outside your network. So, every user, device, and connection is treated as potentially compromised until proven otherwise. This approach protects organizations from modern cyber threats, enabling them to operate and grow with confidence, knowing that their security posture adapts to new technologies and evolving risks.
Why Zero Trust Matters
Cybersecurity has always been a moving target, but today’s challenges are unprecedented. Cloud-first businesses face risks that perimeter firewalls and VPNs were not designed to handle. Employees are logging in from coffee shops and home offices; contractors and vendors often need privileged access; applications span data centers and public cloud platforms, which has turned each connection into a potential entry point for attackers.
Zero Trust is not just another layer of security, but a strategic shift in the approach to security. By verifying every request and limiting access based on context, organizations can reduce their attack surface while maintaining agility. For medium to large enterprises managing thousands of users and devices, this approach offers three critical advantages:
Modernized Security Posture: Continuous verification and risk-based controls prevent unauthorized access, even when credentials are stolen or systems are compromised.
Protection of Critical Assets: Micro-segmentation and least-privilege policies create strong boundaries around sensitive data, ensuring compliance with regulations like GDPR, HIPAA, and PCI DSS.
Confidence to Scale: With Zero Trust in place, IT teams can adopt cutting edge technologies, deploy new apps, and support hybrid work without exposing the organization to unnecessary risk.
What Is Zero Trust Architecture?
At its core, Zero Trust is a security framework that treats every access request as untrusted until validated. Unlike perimeter-based models, it does not automatically trust users or devices inside the corporate network. Instead, Zero Trust enforces continuous authentication and authorization for every session, whether the user is working remotely, connecting via a personal device, or sitting at headquarters.
Key elements of a Zero Trust environment include:
Identity-centric access - Access decisions are based on user identity, device health, location, and other risk factors.
Micro-segmentation - Networks are divided into smaller zones to contain potential breaches and limit lateral movement.
Continuous monitoring - User and device behavior is constantly analyzed to detect anomalies in real time.
Least privilege - Users receive only the access necessary to perform their tasks, and nothing more.
This “perimeter-less” approach is especially relevant for organizations embracing hybrid cloud, SaaS, and IoT technologies, where a fixed network edge no longer exists.
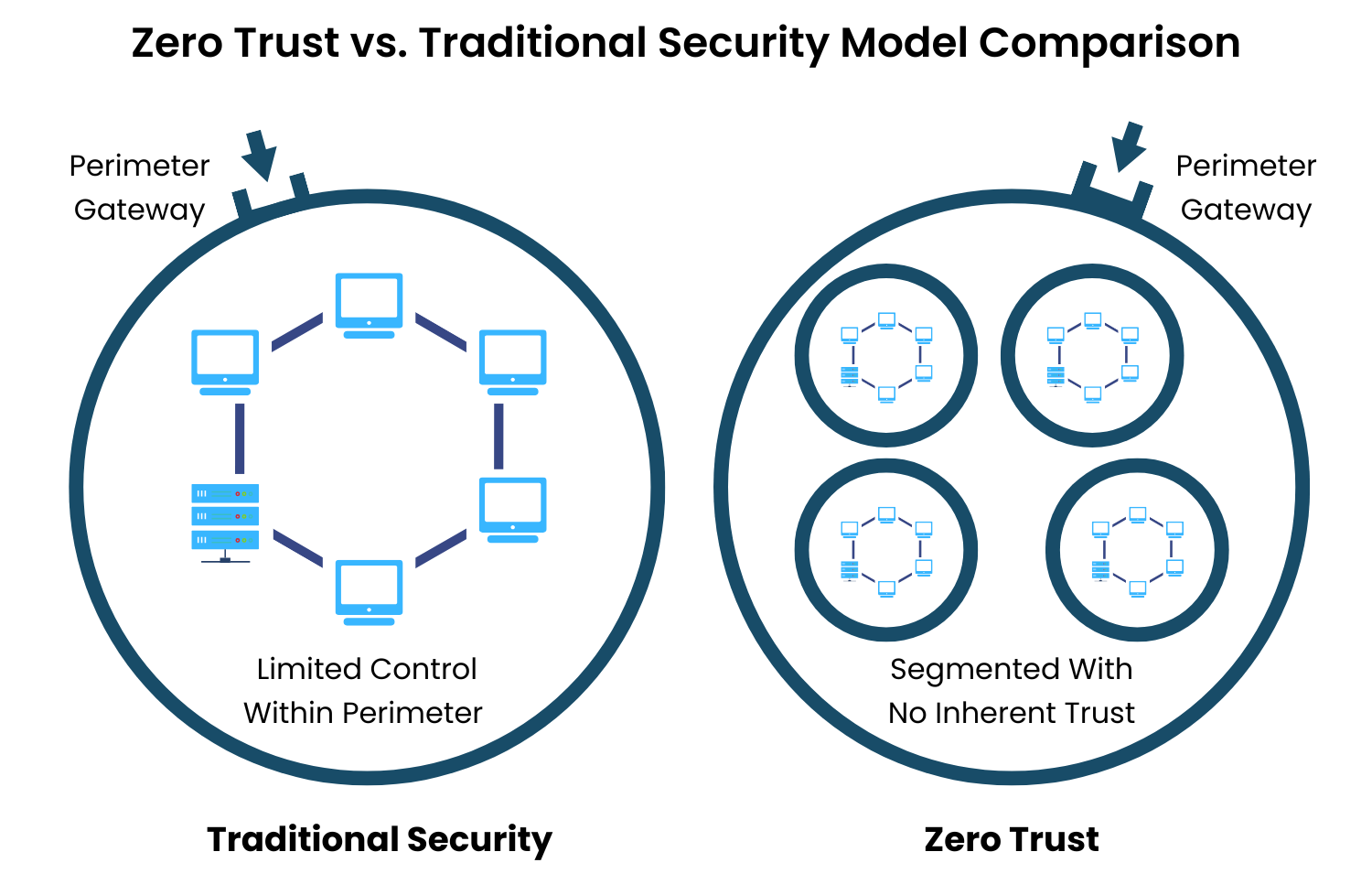
Zero Trust vs. Traditional Security Models
Traditional perimeter-based security treats the internal network as a “trusted zone,” relying on firewalls and VPNs to prevent outsiders from gaining access. Once inside, users and devices typically enjoy broad access. While effective in the era of on-premises infrastructure, this model breaks down in a cloud-first world.
Zero Trust flips that script, disregarding trust based on location, and validating every interaction, every time. Access is granted dynamically, and policies follow users and workloads wherever they go, whether in a data center, a public cloud, or a remote laptop. This shift drastically reduces the likelihood of lateral movement and large-scale breaches.
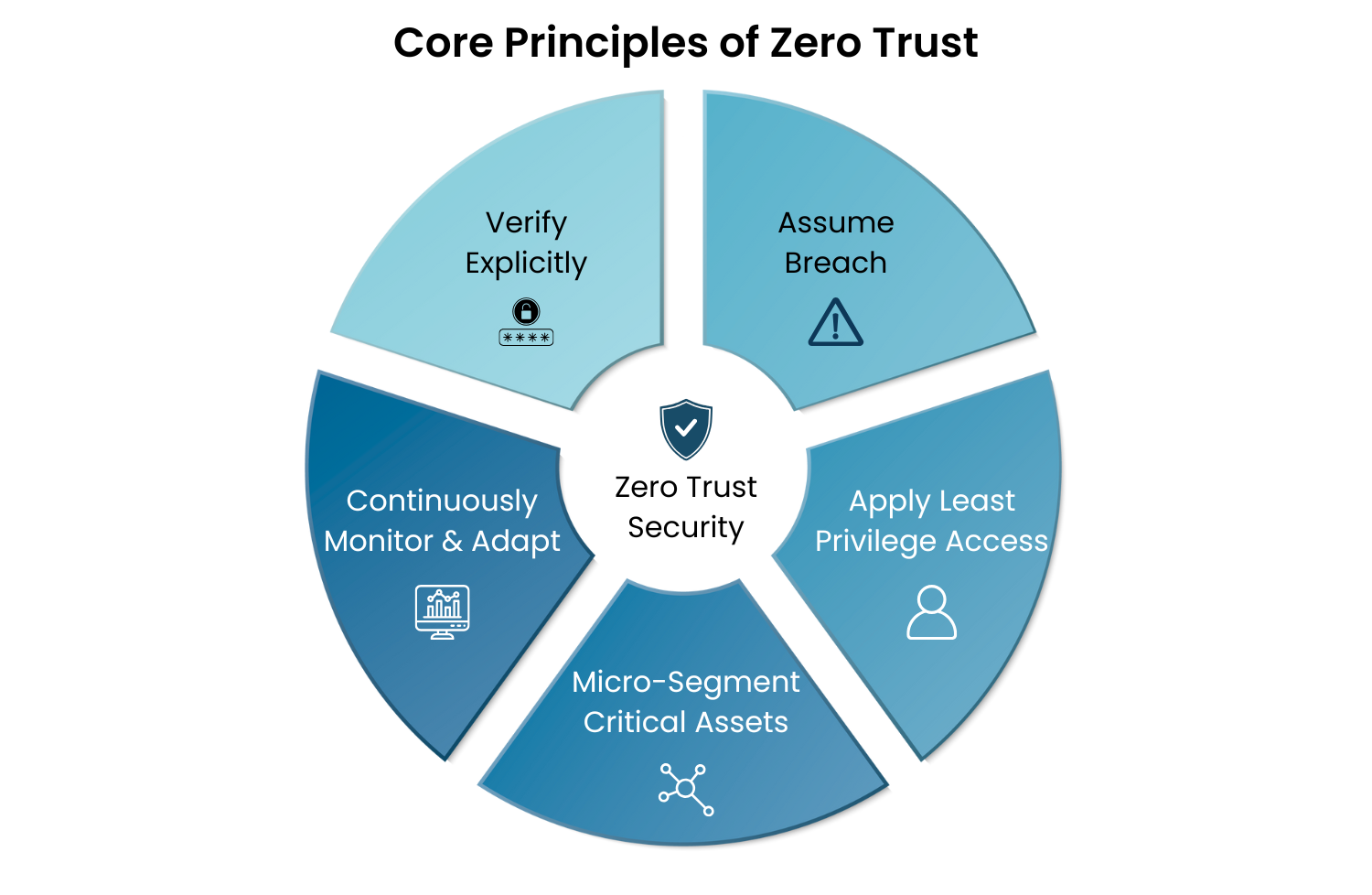
Core Principles of Zero Trust
To implement Zero Trust effectively, it’s important to understand the guiding principles that shape every decision:
Verify Explicitly: Authenticate and authorize every request based on all available data, user identity, device health, location, and behavior patterns.
Apply Least Privilege Access: Grant the minimum permissions required for each role or task, reducing the blast radius if an account is compromised.
Assume Breach: Operate as if an attacker is already inside the network. Segment resources, monitor continuously, and respond rapidly to anomalies.
Micro-Segment Critical Assets: Create granular perimeters around sensitive systems so that even if one area is breached, attackers cannot move freely across the network.
Continuously Monitor and Adapt: Use analytics and automated responses to detect threats, enforce policies, and adjust access controls in real time.
These principles form the backbone of a resilient security culture.
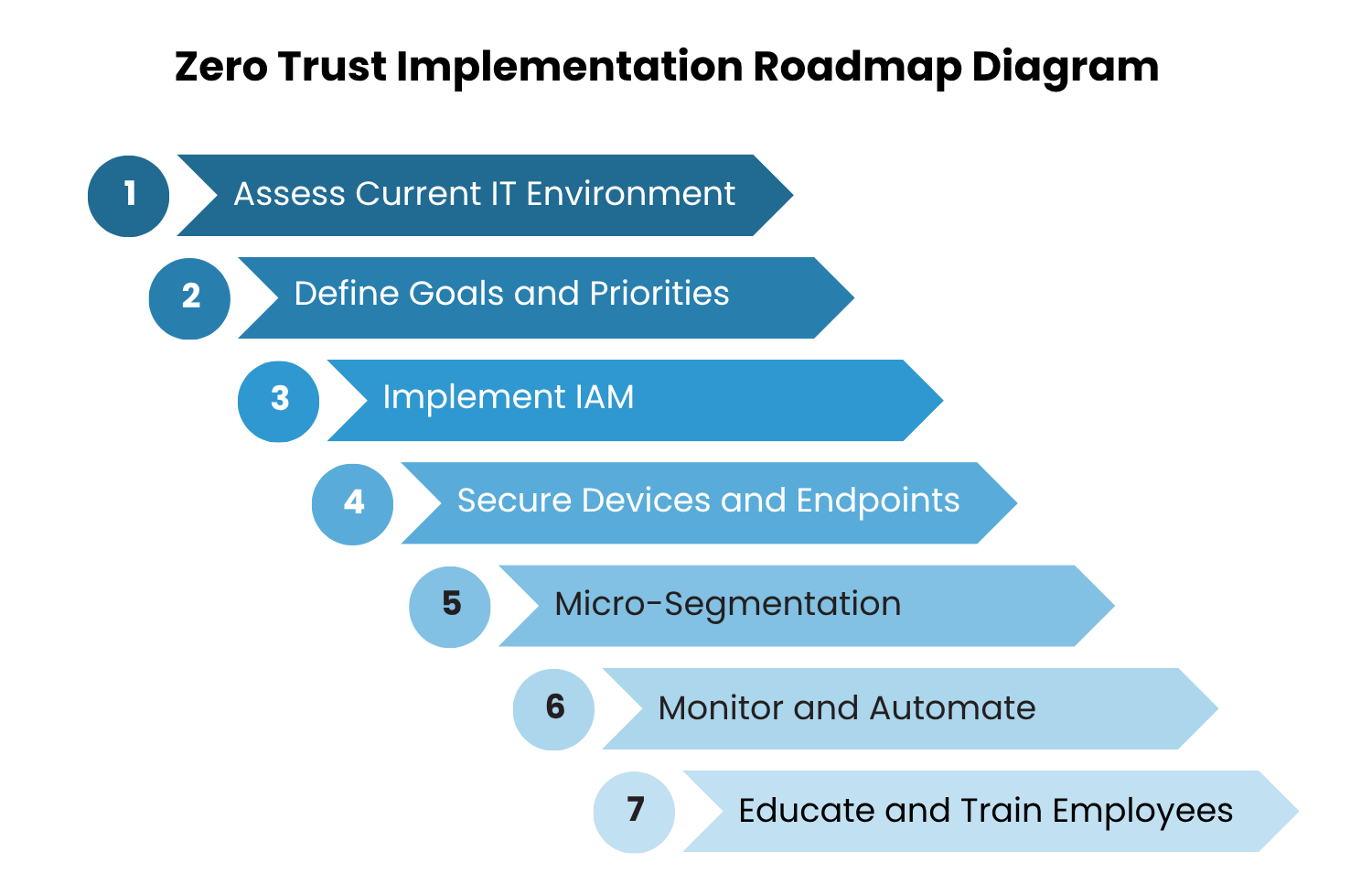
Practical Roadmap to Zero Trust Implementation
Adopting Zero Trust is not an overnight project. It’s a phased journey that combines technology, policy, and cultural change. Here is a practical roadmap that balances strategic vision with actionable steps:
Step 1: Assess Your Current Environment
Begin with a comprehensive audit of your IT landscape. Catalog all assets, including networks, devices, applications, and data flows. Evaluate current security controls such as firewalls, encryption, and endpoint protection. Use vulnerability scanning to identify weak points like unpatched systems or overly permissive access rights.
This discovery phase reveals gaps and establishes a baseline for measuring progress.
Step 2: Define Goals and Priorities
Next, align your Zero Trust strategy with business objectives. Are you focused on securing a hybrid workforce, protecting intellectual property, or achieving regulatory compliance? Setting clear priorities allows you to allocate resources effectively and measure success through metrics like reduced unauthorized access or improved compliance scores.
Step 3: Strengthen Identity and Access Management (IAM)
Identity is the new perimeter. Deploy multi-factor authentication (MFA) across all accounts, including contractors and vendors. Implement role-based access control (RBAC) so employees only access the resources required for their role. Adaptive MFA, adjusting verification requirements based on context such as device type or location, adds another layer of protection without sacrificing usability.
Step 4: Secure Devices and Endpoints
Every device is a potential entry point. Maintain an up-to-date inventory of all endpoints, including BYOD devices. Enforce security baselines such as encryption, patching, and antivirus. Deploy Endpoint Detection and Response (EDR) tools to monitor real-time behavior and flag suspicious activity before it escalates.
Step 5: Deploy Micro-Segmentation
Limit the damage of a potential breach by dividing your network into isolated segments. Use VLANs, software-defined networking (SDN), or Zero Trust Network Access (ZTNA) to control traffic between workloads. Apply strict access policies and monitor east-west traffic (movement within the network) to detect unauthorized lateral movement.
Step 6: Implement Continuous Monitoring and Automation
Zero Trust is not a “set it and forget it” solution. Use Security Information and Event Management (SIEM) and Security Orchestration, Automation, and Response (SOAR) tools to analyze logs and automate responses. Machine learning can flag unusual patterns, like a privileged user logging in from two locations simultaneously, and trigger automatic containment.
Step 7: Educate and Train Employees
Technology alone cannot guarantee security. Conduct regular cybersecurity awareness campaigns and phishing simulations to help employees recognize and report suspicious activity. Integrate Zero Trust principles into onboarding and provide refresher courses to maintain a culture of vigilance.
Cost-Effective Tools to Accelerate Zero Trust
Implementing Zero Trust doesn’t always require a massive budget. Many cost-effective solutions help organizations build a strong foundation:
Identity and Access Management
Okta offers cloud-based Single Sign-On (SSO), MFA, and adaptive access controls, while Azure Active Directory integrates seamlessly with Microsoft ecosystems for conditional access and identity protection.
Endpoint Detection and Response (EDR)
CrowdStrike Falcon and SentinelOne deliver real-time threat detection and automated remediation, ensuring endpoints remain secure even in distributed environments.
Micro-Segmentation
Illumio provides workload-level security policies that prevent lateral movement and protect sensitive data flows.
Unified Threat Management (UTM)
Solutions like Fortinet FortiGate or Sophos UTM consolidate firewalls, intrusion detection, and malware protection into a single, manageable platform.
Zero Trust Platforms
Cloudflare One and Zscaler offer integrated Zero Trust network access, secure web gateways, and continuous monitoring, that are ideal for organizations seeking end-to-end solutions.
For organizations lacking in-house expertise, Managed Detection and Response (MDR) services such as Blackpoint Cyber provide 24/7 monitoring and rapid incident response, complement internal teams and enhance Zero Trust defenses.
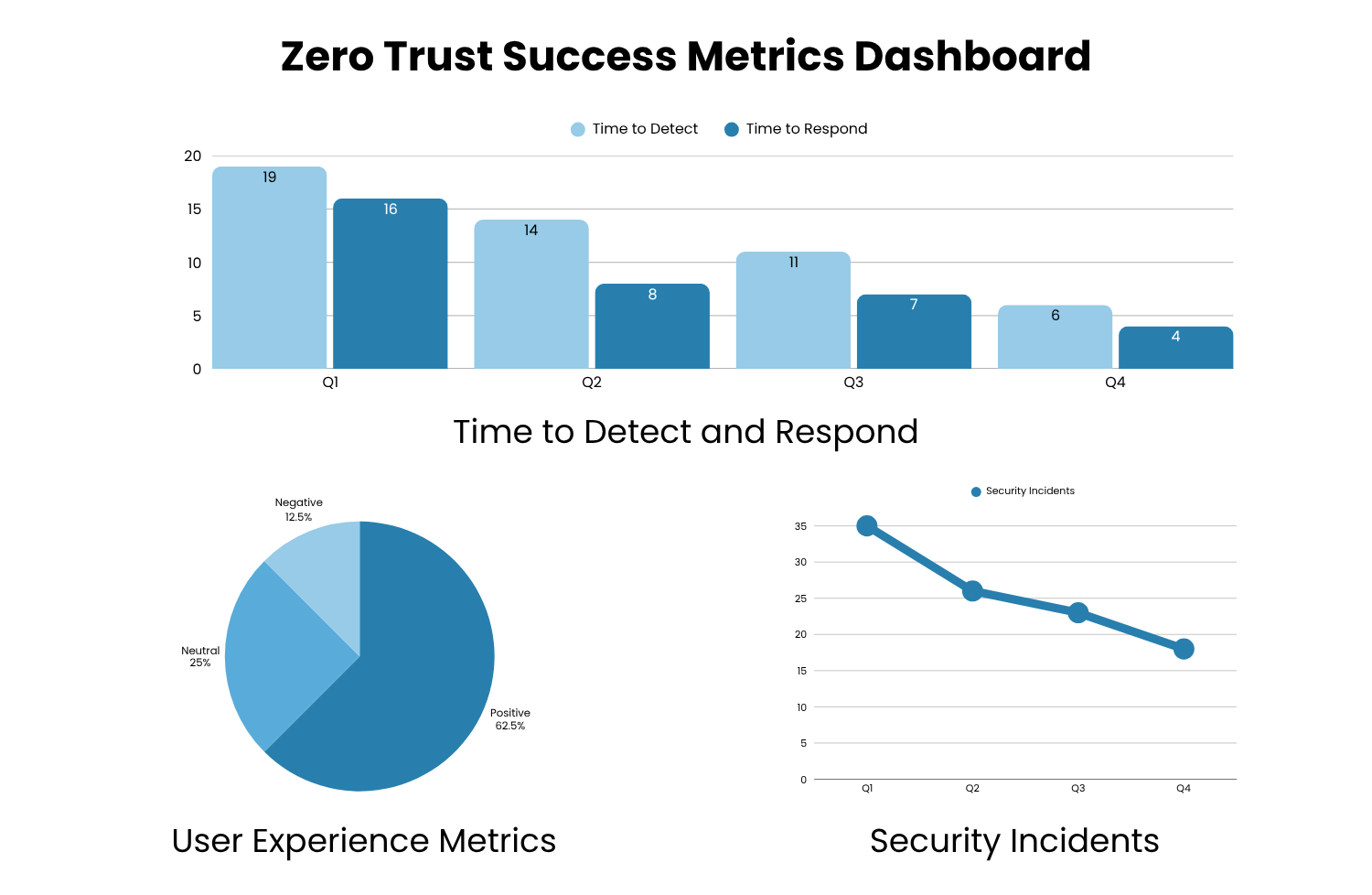
Measuring Success: Key Performance Indicators (KPIs)
Like any strategic initiative, Zero Trust must deliver measurable results. Track the following KPIs to evaluate effectiveness:
Reduction in Security Incidents – Monitor declines in unauthorized access attempts or successful phishing attacks using tools like Okta or CrowdStrike.
Time to Detect and Respond – Measure Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). Automated alerts and AI-driven analytics should reduce these numbers over time.
Compliance Audit Results – Track audit findings, remediation timelines, and progress toward certifications like SOC 2 or ISO 27001.
User Experience – Measure reductions in access-related IT tickets and provisioning times. A well-designed Zero Trust environment should improve both security and productivity.
Competitive Advantages Beyond Security
While Zero Trust is fundamentally about protecting data, its benefits extend well beyond cybersecurity:
Faster Innovation – With security policies that adapt to new applications and workloads, IT teams can adopt cloud services and deploy new technologies without lengthy security reconfigurations.
Improved Customer Trust – Demonstrating strong security practices builds confidence among clients, partners, and regulators, which gives a competitive advantage in industries like finance, healthcare, and e-commerce.
Operational Efficiency – Automation and centralized management reduce administrative overhead, allowing IT teams to focus on strategic initiatives rather than manual security tasks.
Therefore, Zero Trust is not just a defensive measure but also a growth enabler.
This blog post is an excerpt from our white paper, Zero Trust Architecture: Practical Implementation For Medium To Large Businesses. It is a more comprehensive guide on Zero Trust and includes sections on the Challenges To Zero Trust Implementation, Real-World Case Studies, and Resources To Help With Zero Trust Implementation.
Conclusion
The shift to Zero Trust may seem daunting, but it’s more manageable than you expect. It is highly likely that you already have some of the building blocks, such as MFA or endpoint protection, in place. The key is to start with high-impact projects, like securing remote access or implementing identity management, and expand incrementally.
As cyber threats continue to evolve, clinging to outdated perimeter defenses leaves businesses vulnerable. Zero Trust provides a future-ready security framework that protects critical assets, supports innovation, and gives executives confidence in an increasingly unpredictable digital world.
Ready to Take the Next Step?
Implementing Zero Trust is a journey, but you don’t have to navigate it alone. At Jones IT, we specialize in helping organizations design, deploy, and optimize Zero Trust strategies tailored to their unique needs and budgets. Whether you’re beginning with identity management, micro-segmentation, or full Zero Trust network access, our experts can guide you every step of the way.
Contact us today to explore how Zero Trust can secure your business and unlock new opportunities, without sacrificing speed, scalability, or peace of mind.