Why Defense Tech Startups Choose Jones IT as Their MSP
Defense technology startups operate in a high-stakes ecosystem where rapid innovation, airtight security, and strict compliance are non-negotiable. As these agile companies push the boundaries of technology with solutions that directly influence national security, even the smallest vulnerability can have far-reaching consequences. The pressure is intense because on one hand, they need to deliver reliable technology quickly, and on the other, they have to navigate a maze of regulatory requirements. This demanding mix of urgency and criticality necessitates a lean, highly efficient operating model.
Despite their technical expertise, many promising startups find themselves pulled away from that mission by IT demands that, while essential, don’t advance their core objectives. Routine but time-consuming tasks like helpdesk requests, compliance upkeep, employee onboarding, and infrastructure management, eat into limited resources and slow the pace of innovation. Every hour spent on IT administration is an hour not spent building the technologies that defense agencies urgently need.
A trusted Managed Service Provider (MSP), like Jones IT can help close this gap. By offloading non-core IT functions to Jones IT, startups free their teams to focus fully on innovation, research, and development. The result is a more focused, agile organization positioned to deliver mission-critical technologies without compromise.
This blog post explores the 5 key IT challenges that Defense Tech startups face and how Jones IT not only relieves these IT pressures, but also reduces costs, minimizes risks, and provides specialized expertise, tailored to the defense sector’s unique security and compliance challenges.
We Understand What Makes Defense Tech Unique
Defense technology startups can’t operate like other companies as they face some of the strictest security, compliance, and operational demands in business. Every decision carries weight, from safeguarding sensitive data to ensuring regulatory adherence. That’s why they need IT partners who understand the unique realities of the defense sector.
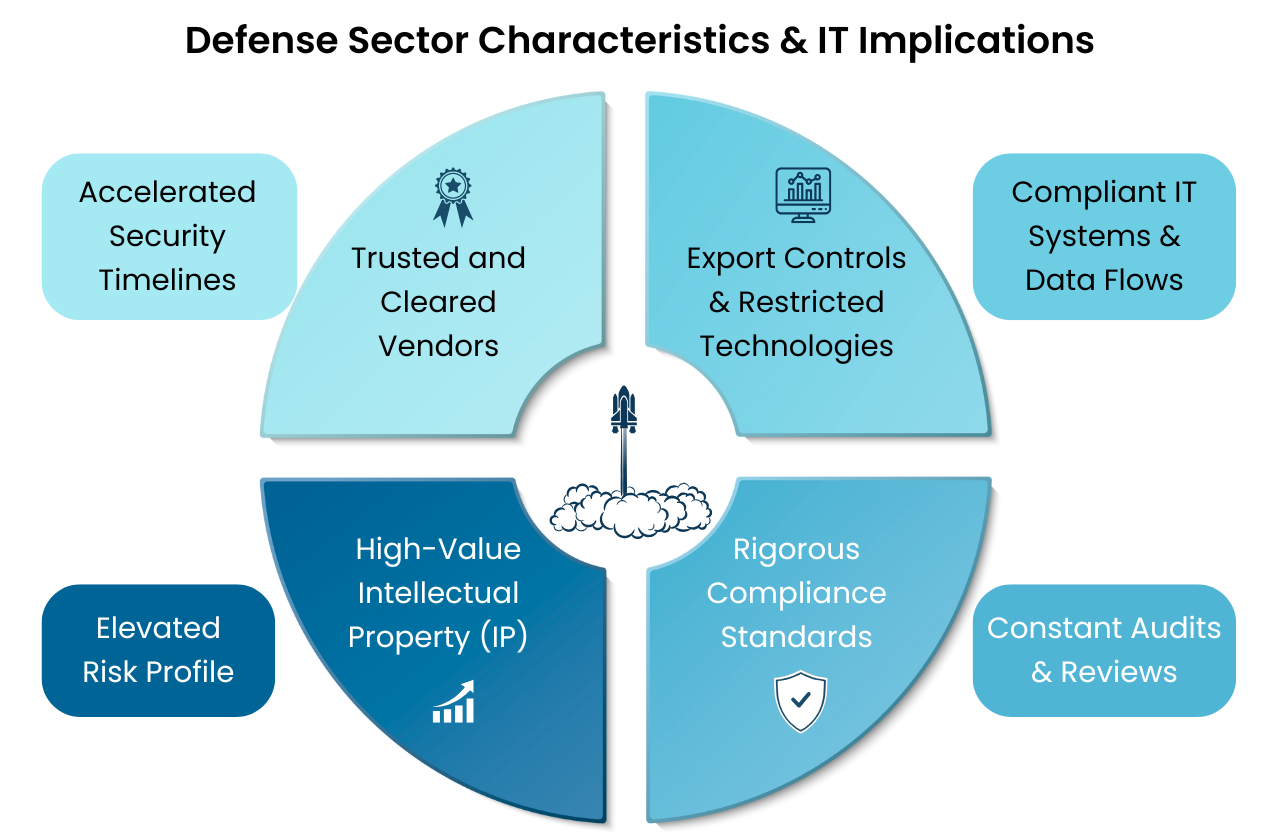
Trusted and Cleared Vendors
Access to classified or sensitive information requires more than technical expertise, it demands cleared or highly trusted vendors who can operate under government-mandated frameworks. Our team is experienced in navigating these environments, ensuring sensitive data stays secure and compliant.
Export Controls and Restricted Technologies
Defense innovations often fall under International Traffic in Arms Regulations (ITAR) and Export Administration Regulations (EAR) export controls, where even small missteps can lead to severe penalties. We understand how these regulations shape IT systems and data flows, helping startups remain compliant while avoiding costly mistakes.
Rigorous Compliance Standards
Frameworks like NIST 800-171, Cybersecurity Maturity Model Certification (CMMC), and Defense Federal Acquisition Regulation Supplement (DFARS) mandate strict cybersecurity practices, documentation, and audits. We help startups implement and sustain the processes required to meet, and stay ahead of, these evolving standards.
Protecting High-Value Intellectual Property (IP)
The IP developed by defense startups is often a prime target for nation-state actors and industrial espionage. We implement and maintain IT security systems with advanced safeguards to keep this sensitive innovation secure.
What This Means for IT
The defense sector’s unique pressures create an IT environment unlike any other:
Accelerated Security Timelines: Security gaps must be closed fast, leaving no margin for error.
Stricter Policies and Procedures: Every action, from access control to incident response, requires rigorous oversight.
Constant Audits and Reviews: Systems must be audit-ready at all times to satisfy regulators and prime contractors.
Elevated Risk Profile: The consequences of failure go far beyond financial loss and can even directly impact national security.
At Jones IT, we’re built for these challenges. Our deep experience working with startups in highly regulated sectors means we deliver managed services that combine efficiency, airtight security, and compliance readiness. With us as a partner, defense startups can stay focused on what matters most – innovating and delivering technologies that protect national interests.
Top IT challenges Defense Tech startups face and how Jones IT delivers the solution:
1. Compliance & Regulatory Requirements
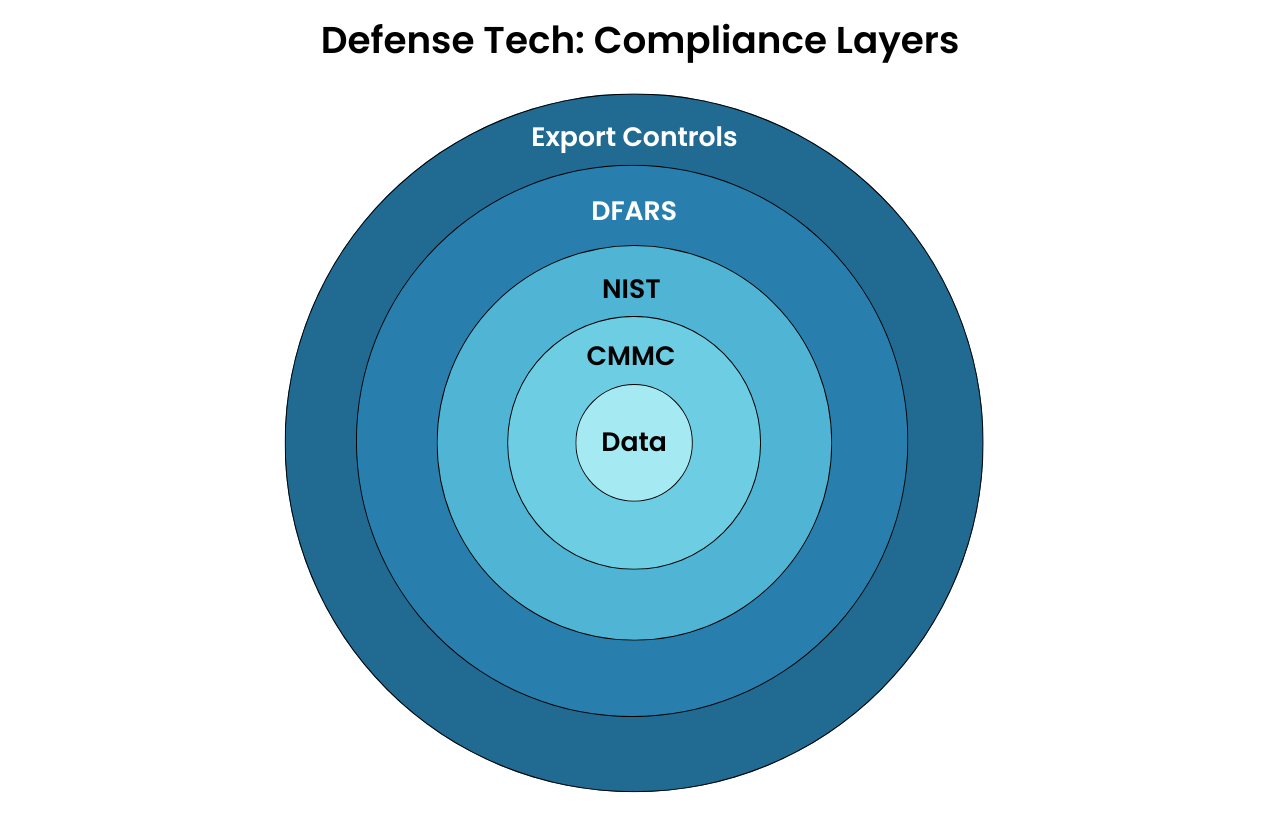
Defense technology startups face some of the strictest regulatory demands of any industry. From cybersecurity controls to export restrictions, the compliance landscape is complex and unforgiving. Key frameworks include:
ITAR (International Traffic in Arms Regulations): Governs the manufacture, export, and temporary import of defense articles, the furnishing of defense services, and brokering activities involving items described on the United States Munitions List (USML).
CMMC (Cybersecurity Maturity Model Certification): Sets the cybersecurity standards required for contractors and their supply chains handling sensitive unclassified information.
DFARS (Defense Federal Acquisition Regulation Supplement): Defines strict requirements for cybersecurity, supply chain risk management, and protection of controlled unclassified information (CUI).
NIST SP 800-171: Establishes detailed guidelines for protecting CUI in nonfederal systems.
Failure to meet these standards can mean more than financial loss, it can lead to blocked contracts, stalled funding, or even the loss of a company’s viability. For startups aiming to innovate quickly, navigating this maze alone can drain resources and slow growth.
How Jones IT Helps With Defense Sector Compliance
At Jones IT, we make compliance a strength rather than a stumbling block. Instead of shouldering the cost of building in-house expertise, defense tech startups can leverage our specialized knowledge and extensive experience for a streamlined, cost-effective path to compliance.
Here’s how we help:
Expert Consulting: We translate complex regulations into practical, actionable strategies tailored to your business.
Audit Preparation: From documentation to system readiness, we ensure you’re always prepared for audits with minimal disruption.
Documentation Management: We handle policies, procedures, and training records, keeping them accurate, current, and audit-ready.
Ongoing Monitoring: With continuous assessments, penetration testing, and threat monitoring, we help maintain compliance long after the initial audit and ready for the next audit.
2. Data Security & Cyber Threats
For defense technology startups, their intellectual property is usually their most valuable asset. Designs, code, and research are incredibly valuable and often carry national security implications, making these companies prime targets for advanced cyberattacks. The threats don’t stop at the perimeter; insider threats and vulnerabilities across the supply chain can be just as damaging. In such an unforgiving environment, strong security is essential to survival, stakeholder trust, and growth.
How Jones IT Helps: Advanced Protection Without The Overhead
Jones IT delivers enterprise-grade cybersecurity tailored for defense tech startups, without the cost of building an internal Security Operations Center (SOC). Our approach combines layered defenses, proactive monitoring, and regulatory expertise to safeguard your most critical assets:
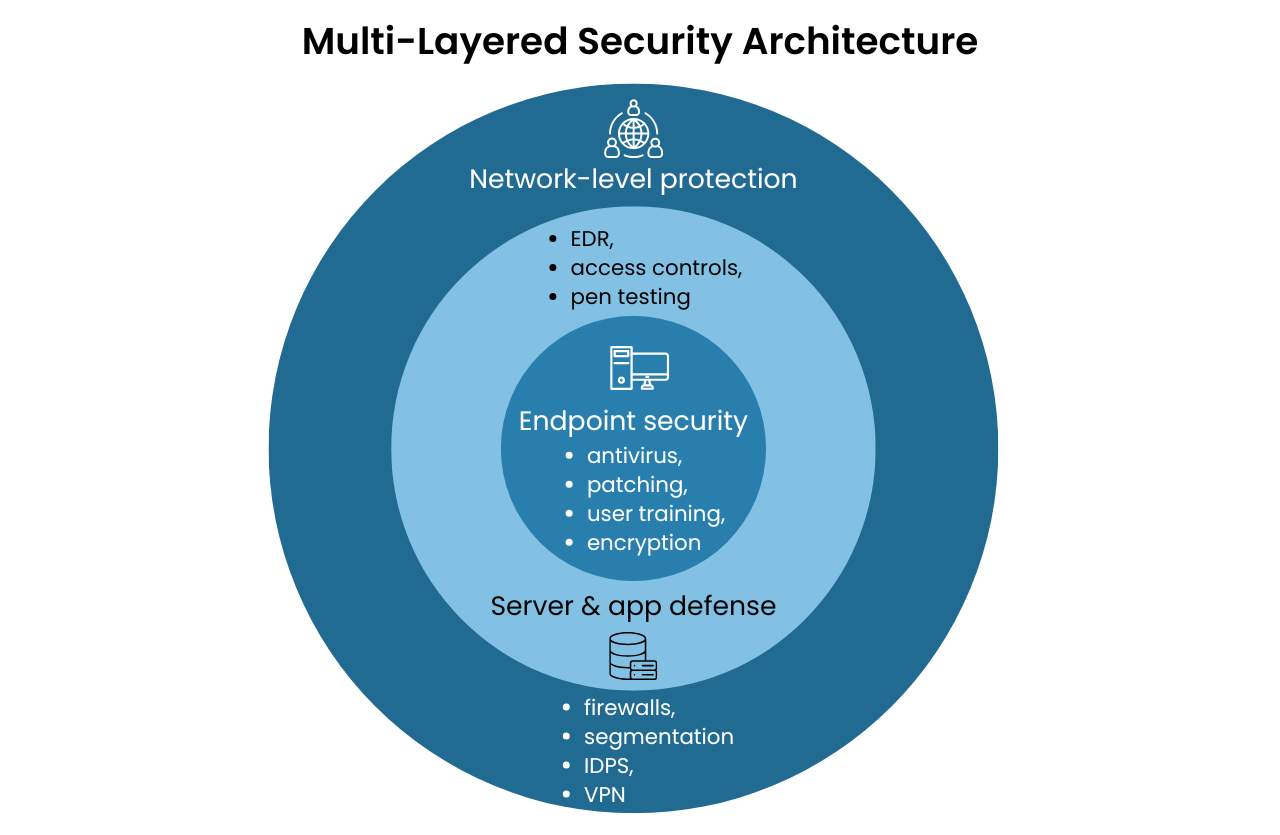
Endpoint Protection: Advanced endpoint detection and response (EDR) tools secure every device, providing real-time threat intelligence and automated remediation against malware, ransomware, and targeted attacks.
Network & Firewall Security: Next-generation firewalls with deep packet inspection, intrusion prevention, and secure VPN access establish a resilient first line of defense.
Intrusion Detection & Prevention (IDPS): Continuous traffic monitoring blocks suspicious activity and known exploits before they escalate.
Proactive Testing: Routine vulnerability scans and penetration testing expose weaknesses before attackers can exploit them, ensuring your defenses stay ahead.
24/7 Monitoring: Our security team leverages Security information and event management (SIEM) to detect, analyze, and respond to incidents around the clock, delivering the assurance of a SOC at a fraction of the cost.
Compliance Alignment: From ITAR and DFARS to NIST and CMMC, we ensure your systems and processes meet the strict regulatory standards defense tech demands.
Employee Training: We equip your workforce with the knowledge to recognize phishing, follow best practices, and strengthen the human layer of defense.
3. Day-to-Day Helpdesk Support
For startups, time is everything: from beating competitors to securing government contracts, everything depends on speed. So, every hour an engineer or R&D specialist spends fixing a laptop, troubleshooting VPN issues, or resolving network connectivity problems is time lost from advancing mission-critical projects. These highly skilled professionals are most valuable when designing, developing, and refining the next generation of defense solutions, not dealing with IT roadblocks. And when project deadlines loom and engineers are overwhelmed, on one hand by deliverables, and on the other, by tickets, IT problems pile up, productivity slows, deadlines slip, and frustration rises across the team.
How Jones IT Helps With Defense-Ready IT Support
Jones IT provides a specialized helpdesk designed to keep defense tech teams operating at full speed. Our support ecosystem removes IT distractions, ensuring your engineers can stay focused on innovation while we handle the rest.
Accessible, Always-On Support: Our multi-channel support: messaging platforms, phone, email, and ticketing systems, makes it easy for your team to get help fast.
Rapid Resolution Times: Our seasoned IT professionals resolve issues quickly and effectively, keeping projects moving without disruption.
Defense-Savvy Teams: Unlike generic IT providers, we understand highly regulated sectors – classified networks, secure development environments, compliance-heavy systems, and specialized software. This expertise ensures precise solutions tailored to your unique environment.
Dedicated Team: Unlike the typical MSP that offers a rotating cast of helpdesk agents, we assign each client a dedicated team of IT professionals, who not only are familiar with your infrastructure but also deeply understand your technology stack and workflows.
4. Employee Onboarding/Offboarding & Device Lifecycle
For fast-growing startups, managing the employee lifecycle and company-issued devices isn’t just about employer branding and employee experience, it’s a security and productivity imperative. Rapid hiring means onboarding must be seamless; any delay slows new hires from reaching full productivity. On the other end, mistakes during offboarding, like lingering access permissions or unreturned devices, can create serious security vulnerabilities. In defense tech, where intellectual property and national security are on the line, even a small oversight can carry outsized risks.
Beyond access control, there’s the ongoing challenge of device lifecycle management (DLM). From procurement and setup to maintenance, refresh cycles, and secure disposal, every step requires careful coordination. Without the right systems, tracking hardware, ensuring compliance, and managing repairs can drain resources and inflate costs.
How Jones IT Helps Seamless Onboarding/Offboarding
At Jones IT, we take the complexity out of employee onboarding/offboarding and device lifecycle management with solutions designed to protect sensitive data, streamline operations, and free your team from repetitive IT tasks.
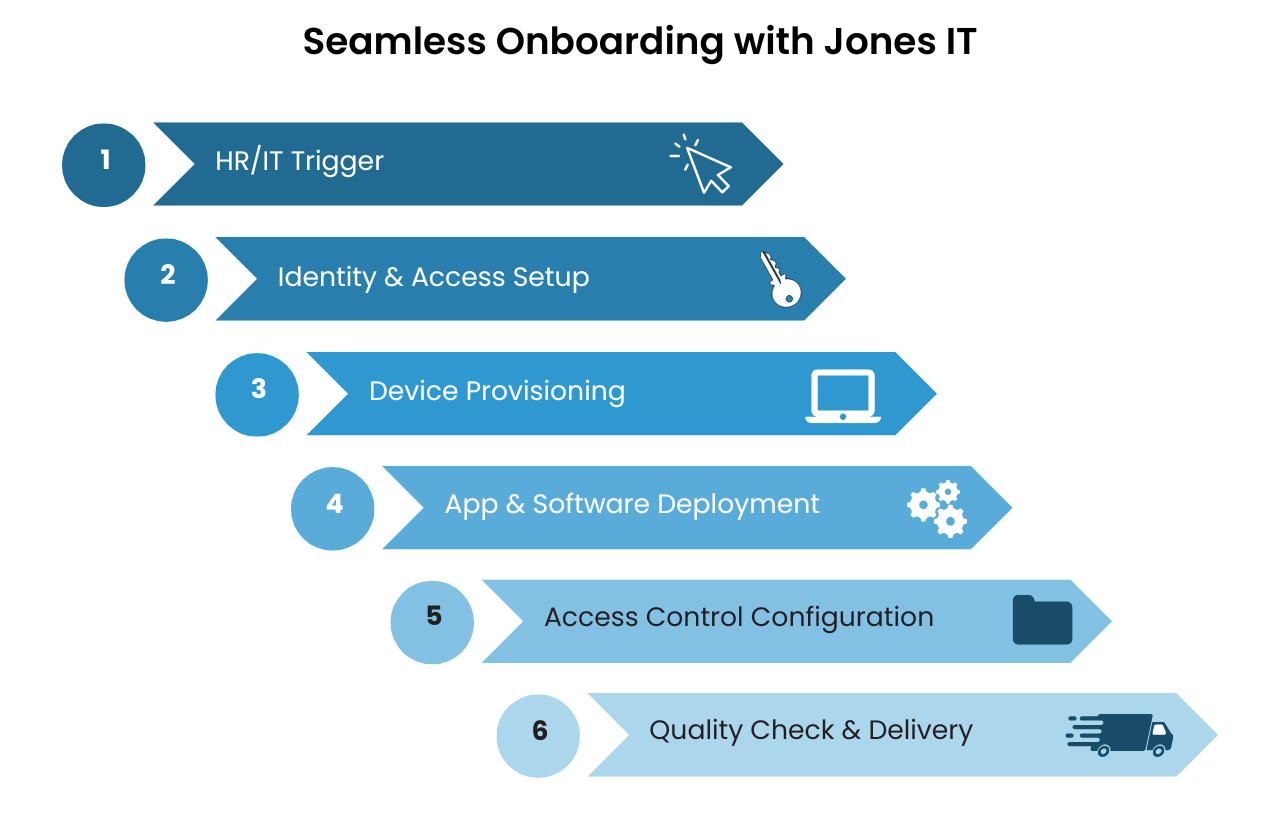
Automated Onboarding & Offboarding: We automate processes to ensure that new hires gain secure access to the tools they need from day one and that departing employees are offboarded securely, with all access revoked. This reduces downtime, eliminates human error, and closes critical security gaps.
End-to-End Device Management: From procurement to precise delivery, we handle every stage of the device lifecycle. Our vendor relationships help reduce lead times, while our security-focused setup ensures devices are deployment-ready the moment they arrive.
Secure Disposal & Compliance: When devices reach end-of-life, we manage secure data wiping and compliant disposal, so sensitive information never falls into the wrong hands.
Accurate Asset Tracking: We maintain real-time inventories of hardware and software licenses, simplifying audits, supporting compliance, and helping plan refresh cycles without surprises.
Reduced Overhead, Lower Risk: By automating workflows and managing IT assets proactively, we cut operational burden while strengthening your security posture. The result: your engineers and leadership can focus on building the future of defense tech, while we ensure your IT runs quietly and securely in the background.
5. Identity & Access Management
For any security-conscious organization, Identity and Access Management (IAM) is a must-have. With hybrid teams, contractors, and strict clearance levels to manage, defense startups face an especially complex security puzzle. Without strong IAM controls, such as least-privilege policies, multi-factor authentication (MFA), and privileged access monitoring, the risk of insider threats or compromised credentials skyrockets. And in this sector, a single lapse can mean stolen IP, compliance violations, or even national security risks.
What’s at stake without robust IAM?
Insider threats: Unregulated access rights create openings for both intentional and accidental misuse.
Compromised credentials: Phishing and weak password hygiene make stolen logins a constant danger.
Data breaches: Sensitive R&D, classified projects, or personnel records could be exposed.
Compliance failures: Falling short of NIST or CMMC requirements risks penalties and lost contracts.
Operational disruptions: Unauthorized access to critical systems can stall R&D and delay milestones.
How Jones IT Helps: Tailored, End-to-End IAM Solutions
At Jones IT, we design IAM strategies purpose-built for defense tech startups, balancing airtight security with operational efficiency. Our approach gives you enterprise-grade protection without the overhead of hiring a full in-house security team.
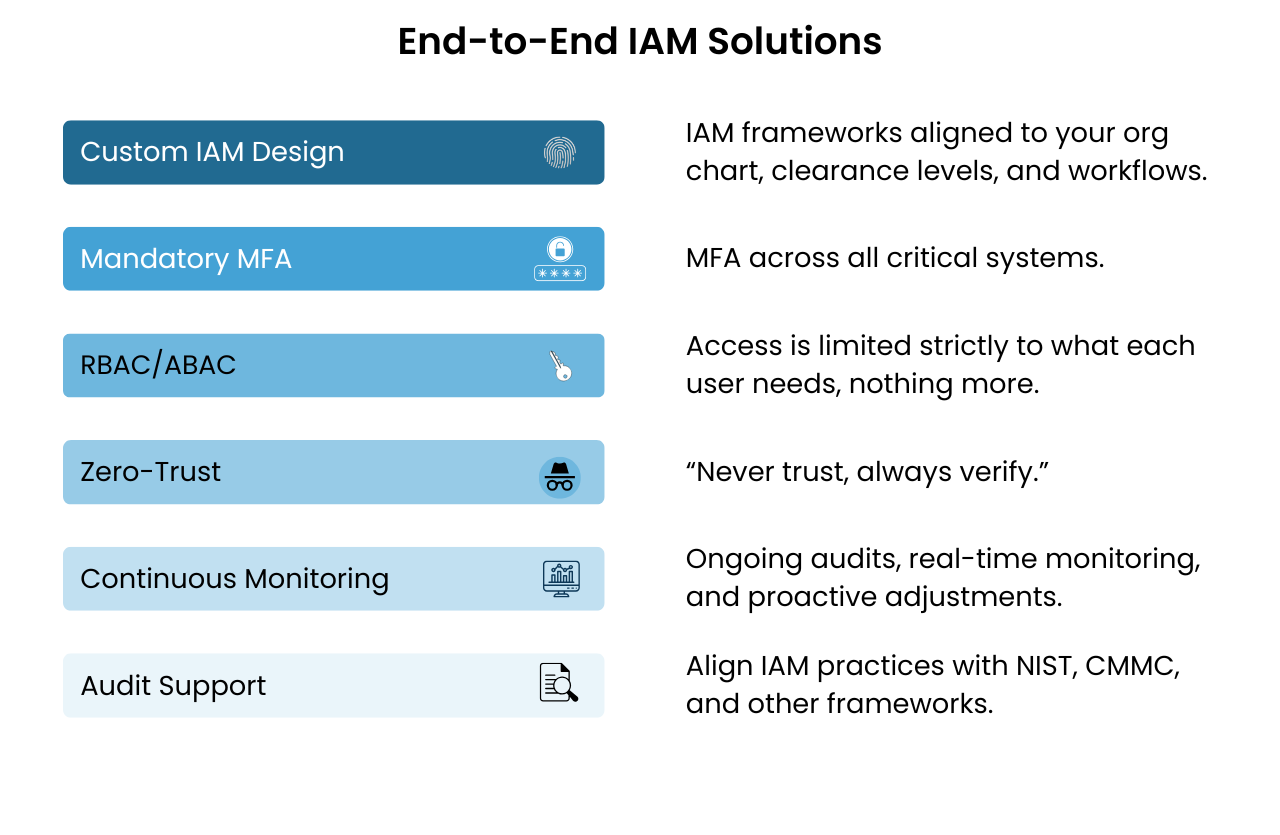
Custom IAM Design & Integration: We build IAM frameworks aligned to your org chart, clearance levels, and workflows, ensuring seamless access while safeguarding sensitive assets.
Mandatory MFA Everywhere: We enforce MFA across critical systems, blocking attackers even if credentials are compromised.
Granular Role & Attribute-Based Controls (RBAC/ABAC): Access is limited strictly to what each user needs, nothing more. As roles evolve, permissions adapt automatically.
Zero-Trust Implementation: For startups ready to lead with advanced security, we guide you through adopting a Zero-Trust model: “never trust, always verify.”
Continuous Monitoring & Optimization: IAM isn’t a one-and-done setup. We provide ongoing audits, real-time monitoring, and proactive adjustments as threats evolve.
Compliance & Audit Support: We align your IAM practices with NIST, CMMC, and other frameworks, backed by the documentation and expertise needed for smooth audits.
Conclusion
Defense tech startups operate in a demanding environment. They have to balance rapid innovation with strict compliance, manage sensitive intellectual property under constant cyber threat, and support highly specialized teams who can’t afford to be bogged down by IT distractions. Add to that the complexities of secure onboarding, device lifecycle management, identity access controls, and an evolving threat landscape, and it’s clear that, in this sector, IT isn’t just an operational function but a key business enabler.
With an MSP partner like Jones IT, IT transforms from a bottleneck into a competitive edge. By delegating non-core IT tasks to us, startups can streamline operations, strengthen security, and ensure compliance, all while keeping their engineers and R&D talent focused on innovation. This shift not only reduces overhead but also improves efficiency, accelerating product development, enhancing resilience, and positioning defense startups to win in a space where execution speed and reliability make all the difference.
Is your defense startup getting bogged down by IT challenges? Schedule a free consultation to discover how we can turn your IT operations into a competitive advantage.