The Real Story of Achieving SOC 2 Compliance: What We'd Do Differently
When we decided to pursue SOC 2 Type 2 compliance at Jones IT, we knew it was necessary. Our clients, especially those in fintech, healthcare, and heavily regulated industries, weren't just asking for our SOC 2 report anymore. They were requiring it.
If you're reading this, you're probably in a similar position. Maybe you're preparing for a Series A, and investors want to see operational maturity. Maybe you're losing deals to competitors who can produce a SOC 2 report. Maybe your biggest prospect just sent over a security questionnaire that made your head spin.
This isn't going to be a post convincing you that SOC 2 is important. You already know that. Instead, we want to share what we actually went through to get there: the obstacles we hit, the mistakes we made, and the lessons we learned that could save you months of headaches.
The Part Nobody Talks About
Everyone talks about the benefits of SOC 2 compliance, but few people talk honestly about the journey. When we started our compliance journey, we'd been managing security for our clients for years. So, naturally, we thought we had a handle on compliance.
We were wrong about how much we didn't know.
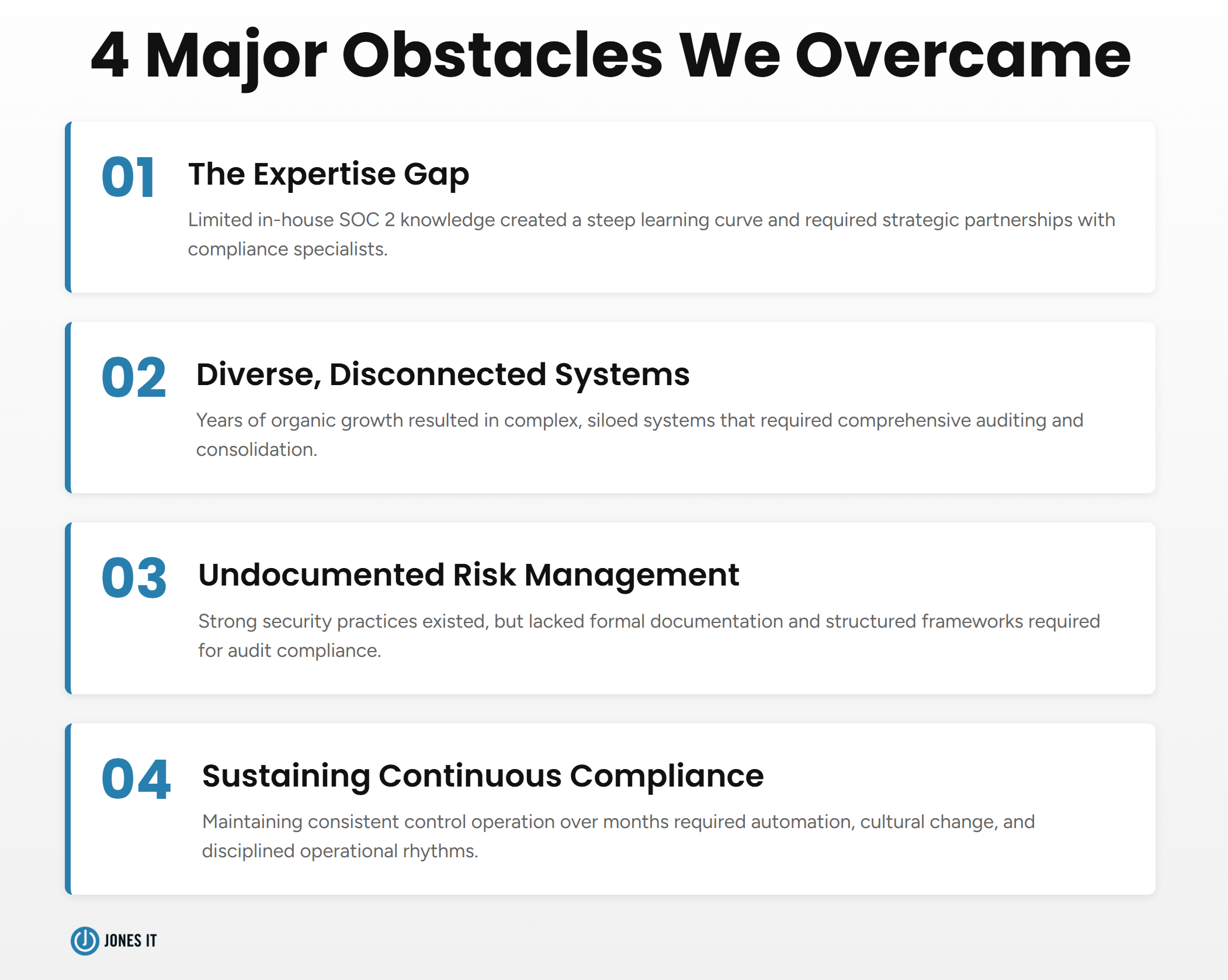
Obstacle #1: The Expertise Gap
Our team included experienced IT security professionals, but SOC 2 compliance is its own beast. Understanding the Trust Services Criteria is different from implementing them. Knowing what evidence auditors need is different from configuring secure systems.
The learning curve was steeper than we anticipated.
What we did about it:
We made a critical early decision to partner with third-party compliance specialists rather than trying to figure everything out ourselves. This wasn't about outsourcing the work; we still had to do the heavy lifting, but about getting the right guidance from people who'd been through dozens of audits.
Simultaneously, we invested in upskilling our internal team. We didn't just want to achieve compliance, but we wanted to build internal expertise so we could maintain it and eventually help our clients with their own compliance journeys.
The lesson: Don't confuse security expertise with compliance expertise. They overlap, but they're not the same. Get help from people who've done this before, and build your knowledge alongside them. The upfront investment in expertise, whether external consultants or training your team, pays for itself in avoided mistakes and faster compliance achievement.
The Part That Almost Derailed Us
Over the years, our systems had evolved organically. We'd adopted new tools as needs arose, integrated different platforms to solve specific problems, and generally built what worked at the time.
The result? A complex patchwork of systems, platforms, and applications that made compliance a nightmare.
Obstacle #2: Diverse, Disconnected Systems
Configuration errors lurked everywhere across our diverse technology stack. Critical information lived in silos. We had overlapping tools that did similar things in different ways. It was functional, but it was far from audit-ready.
The fragmentation created two major problems:
Security risks from inconsistent configurations across platforms
Operational complexity that made demonstrating continuous compliance nearly impossible
What we did about it:
First, we conducted a comprehensive internal IT audit. This wasn't fun. We mapped every system, application, and platform we used. We identified overlaps, redundancies, and gaps. We documented how everything connected (or didn't connect).
Then we made hard decisions about consolidation. We adopted centralized management frameworks that could handle configurations, access controls, and security policies across our entire environment. We standardized wherever possible without sacrificing the flexibility we needed.
The lesson: Before you dive into compliance, audit your IT environment ruthlessly. You'll discover problems you didn't know existed, and it's better to find them before an auditor does. Consolidation and standardization aren't sexy, but they're foundational. The time you spend cleaning up your systems will dramatically reduce the time you spend gathering evidence later.
The Part That Felt Like Starting From Scratch
We'd been managing risk for years, but mostly in our heads and through informal processes. We knew who had access to what. We understood our vulnerabilities. We had incident response procedures that everyone followed.
The problem? None of it was formally documented.
Obstacle #3: Undocumented Risk Management
SOC 2 requires demonstrable, repeatable processes with clear documentation. "We handle it" isn't good enough. Auditors need to see structured frameworks, documented methodologies, and evidence trails.
Our informal approach had worked when we were smaller, but it didn't meet compliance requirements.
What we did about it:
We initiated a formal risk assessment process that went beyond our existing practices. We evaluated assets systematically, identified potential attack vectors, assessed the likelihood of exploitation, and documented everything.
More importantly, we created clear ownership and assigned specific team members and departments to oversee the identification, assessment, and mitigation of different types of risks. This created accountability that our informal system lacked.
Then we documented it all. Every process. Every methodology. Every decision criterion. This was tedious, but it forced us to think clearly about what we were actually doing and why.
The lesson: Start documenting before you think you need to. If you're planning to pursue SOC 2 in the next 12-18 months, begin formalizing your processes now. Create templates for risk assessments. Document your incident response procedures. Write down how you make decisions about access controls. Your future self will thank you when audit time comes.
The Part That Required the Most Discipline
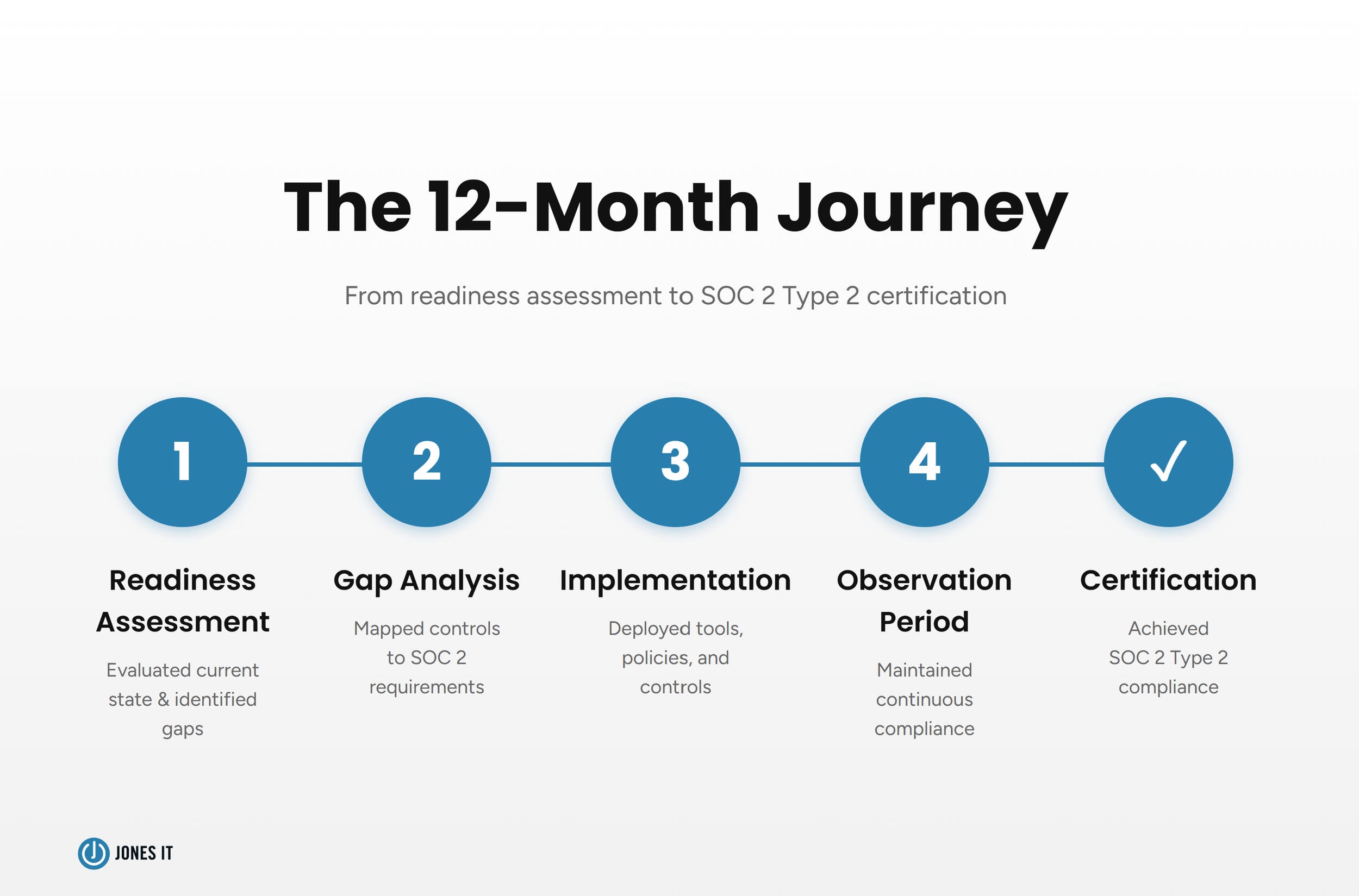
Tools and documentation can only take you so far. SOC 2 Type 2 compliance requires demonstrating that you've operated controls consistently over a minimum observation period (typically 3-6 months, but we ran ours for 12 months to be thorough).
That meant we couldn't just implement the right systems, but had to use them correctly, every single time, for months.
Obstacle #4: Sustaining Continuous Compliance
It's one thing to set up monitoring systems. It's another thing to actually monitor continuously, respond to alerts promptly, and document everything along the way.
Early on, we struggled with consistency. Someone would forget to log an incident response. A quarterly access review would get delayed. Evidence that should have been automatically collected would slip through the cracks.
What we did about it:
We invested heavily in compliance management systems (we used both Vanta and Drata at different points) and automated everything we possibly could. Automated evidence collection. Automated monitoring. Automated reminders for reviews and attestations.
But automation wasn't enough. We also had to build a compliance-conscious culture. We ran regular training sessions, not just once during onboarding, but ongoing refreshers. We made compliance part of our regular team meetings. We celebrated wins when we hit compliance milestones.
Most importantly, we established clear rhythms: weekly security reviews, monthly access audits, and quarterly policy reviews. These rhythms became habits, and habits became culture.
The lesson: Compliance is a marathon, not a sprint. You need systems that make the right thing the easy thing. Automate evidence collection so it happens whether people remember or not. Build compliance into your regular operational rhythms rather than treating it as a separate project. And invest in culture; people need to understand not just what they should do, but why it matters.
The Unexpected Part
We expected SOC 2 to help with sales and client trust. What surprised us was how much it improved our internal operations.
The formal risk assessment process uncovered vulnerabilities we'd been living with unknowingly. Implementing proper access controls through Okta dramatically reduced the time we spent managing permissions (down 70%!). Establishing structured incident response procedures cut our average response time from 8 hours to 2 hours.
These weren't just compliance wins; they were operational improvements that made us more efficient and more secure.
The documentation we created for auditors became valuable operational documentation. New team members could be onboarded faster because processes were clearly written. When incidents occurred, we had playbooks to follow rather than figuring things out on the fly.
The lesson: Don't think of compliance as purely overhead. If you approach it thoughtfully, the work you do to achieve compliance should make your company operationally stronger. If it doesn't, you're probably implementing the wrong controls or implementing the right controls the wrong way.
The Numbers That Mattered
After 12 months of effort, we achieved SOC 2 Type 2 compliance. But the real story isn't just in the certification, it's in what changed:
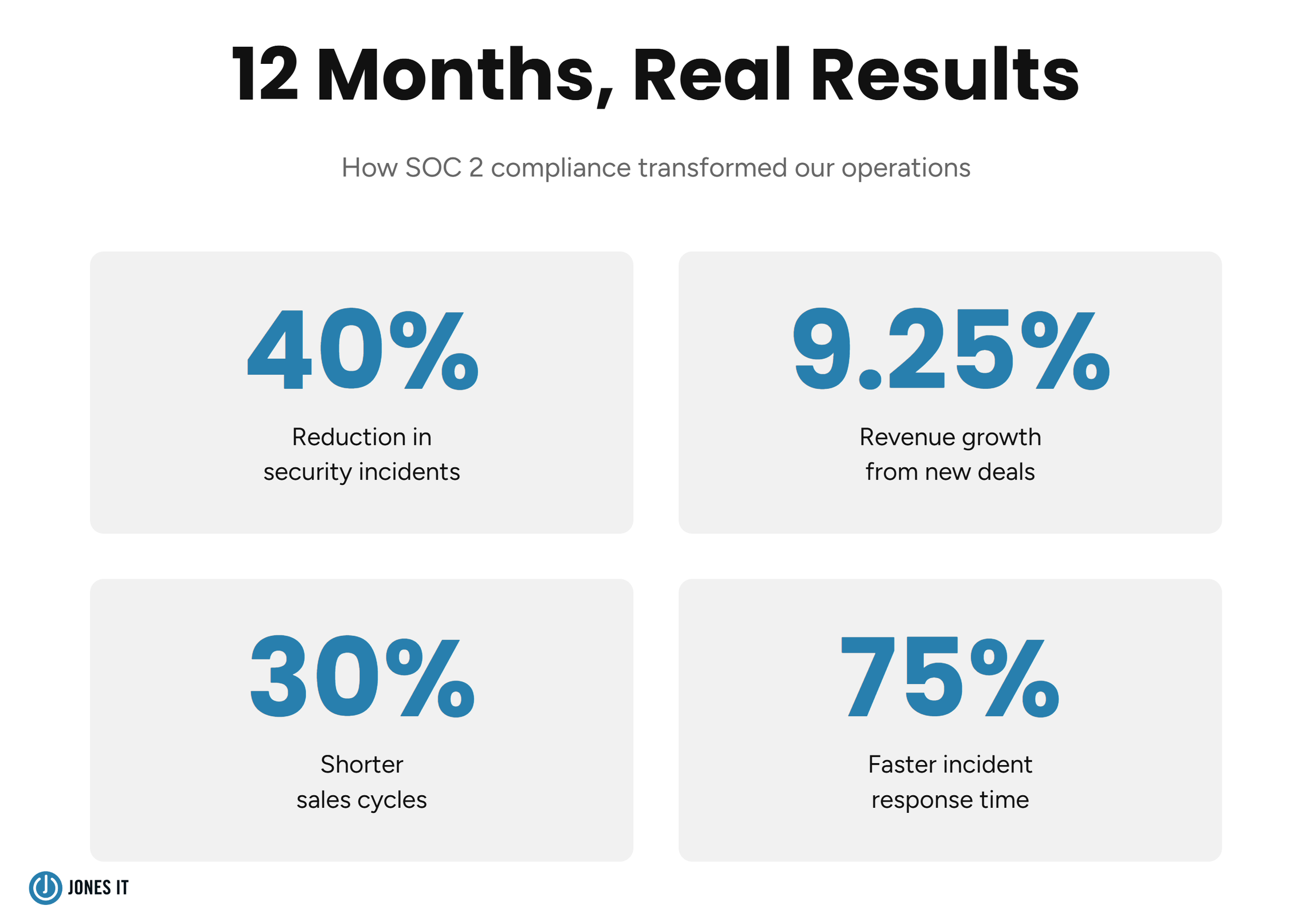
Security incidents dropped 40% in the first year post-compliance, thanks to proactive monitoring and improved endpoint protection.
Sales cycles shortened by 30% because we could hand prospects our SOC 2 report instead of going through extensive security reviews.
Revenue grew 9.25%, directly attributable to deals we won because of our compliance status.
Incident response time fell 75% (from 8 hours to 2 hours average) due to structured procedures.
Access management became 70% faster after we automated provisioning and de-provisioning.
Audit preparation became 50% less time-consuming because we maintained audit-ready documentation continuously.
These aren't hypothetical benefits, but real operational improvements we measured.
What We'd Do Differently
Looking back, here's what we wish we'd known at the start:
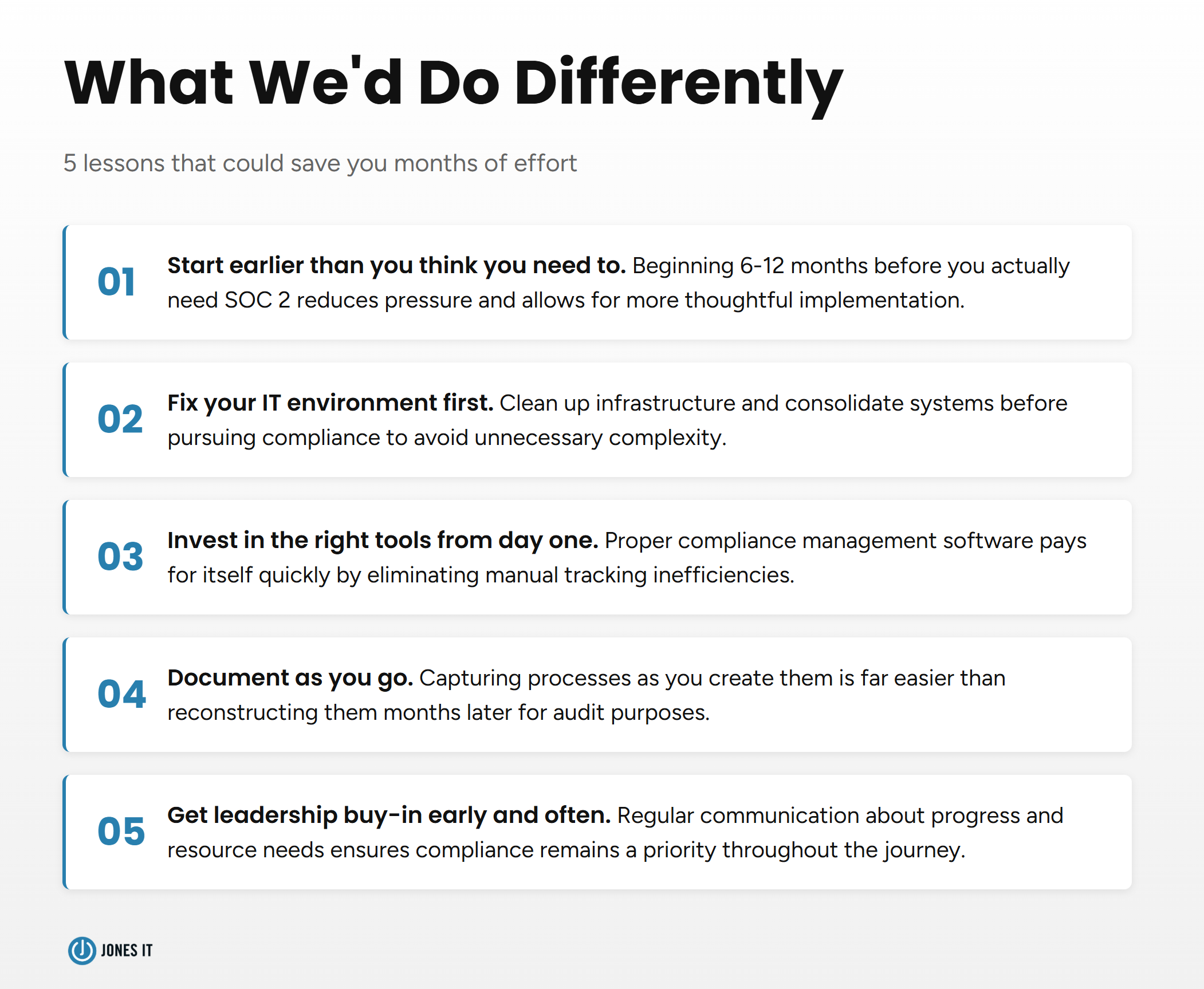
1. Start earlier than you think you need to. We began our compliance journey when clients were already asking for our SOC 2 report. Starting 6-12 months earlier would have reduced pressure and allowed us to be more thoughtful.
2. Fix your IT environment first. We tried to pursue compliance while simultaneously consolidating our systems. This added unnecessary complexity. Clean up your infrastructure, then pursue compliance.
3. Invest in the right tools from day one. We initially tried to track everything in spreadsheets before adopting proper compliance management software. The time we wasted on manual tracking would have more than paid for the tools.
4. Document as you go. We did a lot of retroactive documentation, trying to capture what we'd been doing informally. It's much easier to document processes as you create them than to reconstruct them months later.
5. Get leadership buy-in early and often. Compliance requires resources: time, money, and attention. Our leadership was supportive, but we’ve noticed that this is not always the case, so it’s better to regularly communicate progress and needs. This isn't a project you can assign to a team and forget about.
Your Turn
If you're staring down a SOC 2 audit, know that it's completely achievable, even if, like us, you're starting with informal processes and a complex IT environment. It won't be easy, but it's probably more doable than it looks from the outside.
The obstacles we faced: expertise gaps, system complexity, undocumented processes, and building sustainable habits, aren't unique to us. There are challenges most companies encounter. But they're all solvable with the right approach, the right tools, and the right mindset.
Want the full details? This blog post covers our key lessons learned, but the complete case study includes our step-by-step process, specific tools we implemented, detailed security policies we developed, and comprehensive breakdowns of our results. Download the full case study here to get the complete playbook.
Ready to start your own compliance journey? We've been where you are, and we've helped hundreds of companies navigate the path to SOC 2 compliance. Whether you need full compliance support or just want to talk through your specific situation, schedule a consultation with our team. We'll help you figure out where you are, where you need to be, and the most efficient path to get there.
Jones IT is a San Francisco-based Managed IT Services provider with over two decades of experience helping startups and scale-ups build secure, compliant, and efficient technology operations. We are SOC 2 Type 2 compliant and help clients navigate their own compliance journeys.