The SME Security Playbook for AI Deployment: From Vulnerability to Advantage
Part 2 of 2: Protecting AI Investments Through Strategic Security
The Uncomfortable Truth About AI and Security
In Part 1, we explored how to deploy GenAI for maximum ROI: from Passive AI integration to Domain-Specific Language Models and AI Agents. But here's the reality most AI adoption guides conveniently ignore: rapid AI deployment without proportional security investment creates organizational vulnerability that can erase any productivity gains.
Geopolitical volatility has forced 60% of business and technology leaders to rank cyber risk investment among their top three strategic priorities. For SMEs deploying AI, this isn't an abstract concern; it's an immediate operational necessity.
The uncomfortable equation: AI capabilities × Security vulnerabilities = Net business risk
Without addressing the security side of this equation, AI adoption doesn't reduce risk, but multiplies it.
Why SMEs Are Prime Cybersecurity Targets
The conventional wisdom that cybercriminals focus on large enterprises with deep pockets is dangerously outdated. SMEs are increasingly targeted precisely because they:
Lack dedicated security teams: Most SMEs rely on generalist IT staff who lack specialized cybersecurity expertise.
Run legacy systems: Budget constraints mean older, unpatched systems remain in production longer, creating known vulnerabilities that attackers can exploit with automated tools.
Serve as supply chain entry points: Sophisticated attackers compromise smaller vendors to gain access to larger enterprise customers, and your security weakness becomes their backdoor to Fortune 500 companies.
Underestimate threat sophistication: Many SME leaders still imagine cybercriminals as individual hackers, not organized operations with nation-state backing and industrial-scale attack infrastructure.
Deploy AI without security integration: New AI systems often bypass established security protocols during rapid deployment, creating unmonitored attack surfaces that traditional defenses don't cover.
The strategic implication: Your security posture is more than just about protecting your own organization; it's about maintaining the trust of customers and partners who depend on your security as part of their risk management.
Strategic Security Focus for AI-Era SMEs
Effective cybersecurity for SMEs doesn’t require matching enterprise budgets. It's more about strategic resource allocation focused on your actual vulnerabilities. Here are the three critical priorities:
1. Prioritize Legacy System Remediation
Your oldest systems represent your highest risk. Legacy applications typically:
Run on outdated operating systems without security patches,
Use deprecated authentication methods,
Lack logging and monitoring capabilities, and
Store data in formats incompatible with modern encryption.
Action plan: Identify which legacy applications lack modern security controls and either:
Upgrade or replace them with current alternatives (often cloud-based SaaS solutions with built-in security),
Isolate them from network access and AI integrations through network segmentation, or
Implement compensating controls (additional monitoring, strict access restrictions, data encryption layers).
Budget reality: Legacy system remediation often seems expensive upfront, but compare the cost to the average data breach response: forensics, legal fees, regulatory fines, customer notification, reputation damage, and lost revenue during downtime. Prevention is dramatically cheaper than response.
2. Secure the Supply Chain
AI implementations often involve multiple vendors: cloud providers, AI platform vendors, data processors, integration partners, and managed service providers. Each represents a potential compromise point.
Audit your vendor ecosystem:
What data does each vendor access? Map all data flows to understand exposure
What security certifications do they maintain? Look for SOC 2, ISO 27001, or industry-specific standards
How would you detect if a vendor was compromised? Do you monitor vendor access patterns?
What's your contingency if a critical vendor suffers a breach? Have backup vendors or migration plans
Critical consideration: Your contract terms should include security requirements, breach notification timelines, liability provisions, and audit rights. Legal agreements are your last line of defense when technical controls fail.
3. Shift from Reactive to Proactive Defense
While 78% of organizations plan to increase cyber budgets in 2026, effectiveness depends on the allocation strategy. Reactive spending on incident response, breach remediation, regulatory fines, etc., returns no value. Proactive spending delivers compounding returns.
Invest in:
Continuous monitoring and threat detection: Automated systems that identify unusual activity before it becomes a breach,
Regular penetration testing and vulnerability assessments: Identify weaknesses before attackers do,
Security awareness training for all staff: Human error causes most breaches; train your first line of defense, and
Automated security testing in AI development pipelines: Build security into AI systems from the start.
Reduce spending on:
After-the-fact forensics and remediation: These costs deliver zero preventive value,
Insurance premiums: High premiums often reflect poor security; invest in prevention to reduce insurance costs, and
Compliance penalties: Implement controls proactively rather than paying fines reactively.
The mindset shift: View cybersecurity spending as operational infrastructure (like accounting systems or facilities) rather than discretionary IT expenses. You wouldn't skip building maintenance to save money; apply the same logic to security.
Strategic Use of Managed Services
The biggest barrier to implementing AI-enhanced cybersecurity isn't technology, but expertise. The global cybersecurity talent shortage means SMEs cannot compete with enterprise salaries for specialized security professionals.
Managed Security Service Providers (MSSPs) offer strategic advantages for SMEs:
Access to specialized expertise without full-time salaries and benefits. A single MSSP contract provides access to security analysts, threat researchers, incident responders, and compliance specialists.
24/7 monitoring and response are impossible for most SME IT teams. Security threats don't respect business hours; MSSPs provide round-the-clock coverage.
Economies of scale on security tools and threat intelligence. MSSPs aggregate purchasing power and threat data across multiple clients, providing SMEs access to enterprise-grade capabilities.
Rapid deployment of security capabilities without lengthy hiring and training cycles. You can be operationally protected within weeks rather than months.
Cost predictability: Fixed monthly fees vs. unpredictable breach costs and emergency consultant rates.
Selecting the Right MSSP
Hiring managed services does not mean you are outsourcing responsibility; your organization remains accountable for security outcomes. Select MSSPs based on:
Industry-specific experience and relevant certifications: Look for providers who understand your sector's regulatory requirements and threat landscape.
Transparent reporting and communication protocols: You should receive regular, understandable reports on security posture, not technical jargon that obscures problems.
Clear SLAs around detection and response times: Define what "immediate response" means in hours/minutes, not ambiguous terms.
Cultural fit and responsiveness to your business needs: The MSSP should function as an extension of your team, not a distant vendor.
Red flags to avoid:
Providers who can't explain services in business terms,
Contracts that lock you in without performance guarantees,
Vendors who promise "complete protection" (impossible; no solution is foolproof),
Services that don't include regular vulnerability assessments.
The Data Integrity Crisis Hiding in Plain Sight
It is not an exaggeration to say that most organizations dramatically overestimate their data security posture. The statistics support the claim, as only 6% of organizations have fully implemented essential data risk measures across their entire enterprise.
These "essential measures" aren't exotic security technologies but foundational practices:
Data classification: Identifying which data is sensitive and requires protection,
Data loss prevention (DLP): Technical controls preventing unauthorized data exfiltration,
Access controls: Ensuring only authorized users can access sensitive data,
Encryption: Protecting data both at rest and in transit, and
Monitoring and logging: Detecting unusual data access patterns.
For SMEs deploying AI, this gap is existential. AI models require access to substantial data, and AI-powered features often process or expose data in new ways. Without fundamental data security controls, AI deployment multiplies risk exposure rather than business value.
The Minimum Viable Data Security Program
For AI-adopting SMEs, here are the non-negotiable basics:
1. Classify Your Data
Not everything requires maximum security. Identify what's truly sensitive:
Customer personally identifiable information (PII),
Financial records and payment data,
Intellectual property and trade secrets,
Strategic plans and competitive intelligence,
Employee records.
Create a simple classification scheme (e.g., Public, Internal, Confidential, Restricted) and label data accordingly.
2. Map Data Flows
Understand where sensitive data lives, how it moves through systems, and who can access it, including AI systems and vendors:
Where is data stored (on-premises, cloud, hybrid)?
Which systems process sensitive data?
Which employees have access to what data?
Which vendors can access your data?
How is data transmitted (email, APIs, file transfers)?
3. Implement Encryption
At a minimum, encrypt sensitive data at rest and in transit. Modern cloud platforms make this relatively straightforward through built-in features.
4. Control and Monitor Access
Use role-based access controls (RBAC) so users only access the data necessary for their roles. Monitor for unusual access patterns that could indicate compromise or insider threats:
Failed login attempts,
Access outside normal hours,
Bulk data downloads, and
Access to systems outside the user's normal scope.
5. Establish Data Retention and Deletion Policies
Don't keep data longer than necessary. Reduced data volume means reduced attack surface. Define retention periods based on:
Legal and regulatory requirements,
Business operational needs, and
Customer expectations around privacy.
Implement automated deletion processes to ensure policies are followed consistently.
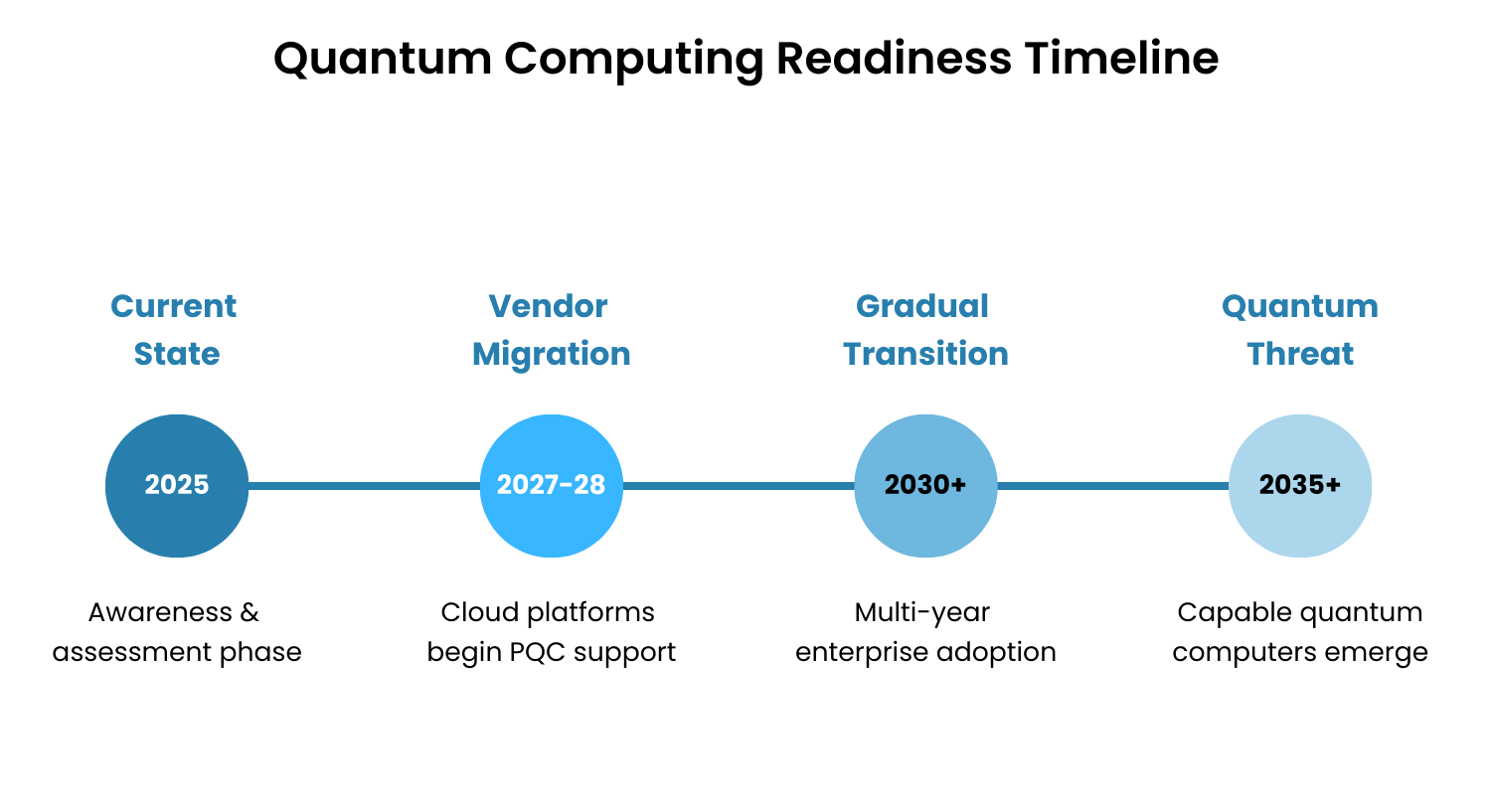
Preparing for Tomorrow's Threats: The Quantum Question
Quantum computing represents a future threat to current encryption standards; quantum computers will eventually break the cryptographic algorithms that are protecting most digital communications and data storage.
The timing paradox: Quantum computers capable of breaking current encryption likely won't exist for another decade, but data encrypted today could be harvested now and decrypted later ("harvest now, decrypt later" attacks). For organizations with long-lived sensitive data, this creates immediate strategic implications.
Post-Quantum Cryptography (PQC) standards are being developed to resist quantum attacks. The National Institute of Standards and Technology (NIST) has published initial PQC algorithms, and migration is beginning.
The Realistic SME Approach to Quantum Readiness
1. Assess Your Cryptographic Dependencies
Identify which systems rely on encryption and where long-term data confidentiality is critical:
What data must remain confidential for 10+ years?
Which systems use public-key cryptography?
What would be the business impact if encrypted data was eventually decrypted?
2. Monitor Vendor Roadmaps
Track when your software and cloud providers will support PQC standards. Major cloud platforms and enterprise software vendors are already planning migrations.
3. Prioritize Immediate Threats
Unless your organization handles state secrets or long-term sensitive intellectual property, traditional cybersecurity threats present far greater near-term risk than quantum attacks. Focus resources accordingly.
4. Plan for Gradual Migration
PQC adoption will span years, not months. Include it in long-term IT planning without diverting resources from current security priorities.
Reality check: Organizations with revenues over $5 billion are currently leading quantum readiness initiatives. For most SMEs, quantum preparedness means awareness and alignment with vendor migrations rather than internal PQC implementation projects.
Sovereignty and Localization
An emerging factor complicating data security is technological sovereignty: the expectation that 65% of governments worldwide will introduce requirements by 2028 mandating that certain data and systems remain within national borders or use domestically-controlled infrastructure.
This trend affects SMEs in multiple ways:
Vendor Selection Complexity: Cloud providers and AI platforms must demonstrate compliance with data localization requirements in your operating regions. Some vendors may not support all regions, limiting your options.
Cost Implications: Multi-region deployments to satisfy sovereignty requirements increase infrastructure costs and operational complexity. You may need separate instances in different countries.
Competitive Dynamics: Domestic vendors may gain regulatory advantages over international competitors, potentially affecting your vendor landscape and negotiating power.
Regulatory Risk: Non-compliance with data sovereignty laws can result in fines, service interruptions, or loss of business licenses in certain jurisdictions.
For SMEs operating internationally: When evaluating AI and cloud vendors, prioritize providers with established regional infrastructure and clear compliance frameworks for data sovereignty requirements. Vendors who've invested early in distributed, compliant architectures will offer lower-risk, more stable partnerships as regulations tighten.
Strategic questions to ask vendors:
In which countries/regions do you maintain data centers?
How do you ensure data doesn't leave specified jurisdictions?
What compliance certifications do you maintain for different regions?
How will you adapt to emerging sovereignty requirements?
Security as Competitive Advantage
Here's the strategic reframe: security isn't a cost center, but a competitive differentiator.
In markets where AI adoption is accelerating, customers and partners increasingly evaluate vendors based on security posture. Organizations that can demonstrate:
Robust data protection practices,
Clear compliance frameworks,
Proactive threat management,
Transparent incident response procedures, and
Strong vendor security requirements.
...win business away from competitors struggling with these challenges.
Security becomes a sales asset when:
Enterprise customers evaluate you: Large organizations conduct vendor security assessments. Strong security shortens sales cycles and reduces procurement friction.
Regulatory compliance matters: In regulated industries, such as healthcare, finance, government, etc., security capabilities are table stakes, and poor security disqualifies you from opportunities.
Data privacy concerns increase: Consumer awareness of privacy issues means security-conscious organizations gain trust advantages.
Competitive bids favor lower-risk vendors: When multiple vendors offer similar capabilities, security posture becomes the tie-breaker.
Your Security Action Plan
Based on everything covered, here's your security roadmap aligned with AI deployment:
Immediate (Weeks 1-4)
Conduct a security audit: Identify legacy systems and unpatched vulnerabilities,
Map data flows: Document where sensitive data lives and who can access it,
Evaluate MSSP options: Get quotes and capabilities from 3-5 providers, and
Implement basic encryption: Enable encryption on cloud storage and communications.
Near-term (Months 2-3)
Select and onboard MSSP: Establish 24/7 monitoring and response,
Remediate critical vulnerabilities: Fix the highest-risk legacy system issues,
Implement access controls: Deploy role-based access and multi-factor authentication, and
Audit vendor security: Review contracts and security postures of critical vendors.
Medium-term (Months 4-6)
Develop a data classification scheme: Categorize all organizational data,
Implement DLP controls: Prevent unauthorized data exfiltration,
Conduct penetration testing: Identify weaknesses before attackers do, and
Train staff on security awareness: Build a human firewall against social engineering.
Ongoing
Monitor and review: Regular security posture assessments,
Update and patch: Systematic vulnerability management,
Test incident response: Quarterly tabletop exercises, and
Track emerging threats: Stay informed on quantum, AI security, and geopolitical developments.
Integration With AI Deployment
Security and AI deployment aren't parallel workstreams. They're integrated components of operational capability.
When deploying Passive AI (from Part 1): Verify that embedded AI features maintain your existing security controls. AI capabilities shouldn't bypass authentication, logging, or data protection.
When adopting Domain-Specific Models: Understand where your data goes for model training or inference. Ensure vendors have appropriate security and can't use your data to train models for competitors.
When implementing AI Agents: Autonomous agents require especially careful security consideration since they act on your behalf with potentially wide-ranging permissions. Implement strict scopes and monitoring.
When using Synthetic Data: Verify that synthetic data truly anonymizes sensitive information and can't be reverse-engineered to reveal source data.
The factory floor analogy from Part 1 applies perfectly to security: digital trust and cybersecurity are the reinforced foundation and security gates. If your factory floor is weak (legacy systems, undertrained staff) or your gates are poorly secured (supply chain vulnerabilities, inadequate monitoring), even the best new machinery won't guarantee resilience or protect your intellectual property.
Conclusion: Security as Strategic Enabler
The organizations that will thrive in the AI era aren't those with the most sophisticated AI capabilities or the largest security budgets. They will be the organizations that understand security and AI adoption as an integrated strategy:
Security enables AI adoption by creating the trust foundation necessary for customers, partners, and employees to embrace AI-powered operations.
AI adoption demands security investment because new capabilities create new attack surfaces that traditional defenses don't cover.
Together, they create a sustainable competitive advantage that compounds over time as organizations build both capability and trust simultaneously.
The market won't wait for SMEs to develop perfect security programs any more than it waited for perfect AI strategies. Competitive advantage belongs to organizations that execute effectively with imperfect information and constrained resources, but execute they must.
The complete equation: Strategic AI deployment + Proportional security investment = Sustainable competitive advantage.
Miss either side, and the equation fails.
Series Conclusion: From Strategy to Execution
Across both parts of this series, we've covered:
Part 1 - Implementation:
Why "wait and see" means competitive obsolescence
ROI-focused deployment starting with Passive AI
Key capabilities: DSLMs, AI Agents, Synthetic Data
Resource optimization through policy support and strategic partnerships
Part 2 - Security:
Why SMEs are increasingly targeted
Strategic security priorities for resource-constrained organizations
The MSSP solution to the skills gap
Data integrity fundamentals and emerging threats
The unified message: The window for deliberate, strategic AI adoption with integrated security is open now. Organizations that execute quickly with focused discipline on both capability and protection will build sustainable advantages. Those that wait for "perfect" conditions will find the market has moved on without them.
The question isn't whether to adopt AI or how to secure it; it's whether you'll execute quickly enough on both dimensions to remain competitive in a market where AI integration is becoming the baseline expectation.
Your move.
Need help harden your security as you implement new technology capabilities? Our team has helped 100s of Bay Area organizations secure their infrastructure and data as they test and implement new technologies. Schedule a free consultation to discuss your specific situation.